92% of internet users watch videos online, with over 1 billion hours of video content watched on YouTube each day. Given this appetite for videos, it’s understandable why video content is foundational to most modern businesses. From fitness coaching, to language learning and digital marketing, businesses in any niche can (and should) be creating their own video content.
However, the widespread distribution of digital video brings significant risks to video owners, primarily unauthorized access and piracy – which threaten revenue and intellectual property.
Digital Rights Management (DRM) is how video owners can protect their videos. Here we discuss DRM, its importance for video creators, and how to best use it to safeguard your digital assets.
What is DRM?
Digital Rights Management (DRM) is the practice of regulating access to, and use of, digital content (videos, audio, or software).
The primary goal of any DRM campaign is to ensure only authorized individuals are able view, copy, or distribute certain content. DRM achieves this by “gating” content using encryption, licensing procedures, and access control systems. It protects creators’ work – while also creating a secure environment where users’ personal and sensitive information is safe.
For video creators in particular, this means that only paying subscribers or approved viewers can access their material, which preserves revenue streams and creative control.
Across industries, DRM is central to many well-known business models. For instance:
- Major streaming services such as Netflix use DRM to encrypt video streams, thus restricting access to active subscribers and viewers in certain locations.
- Online learning platforms such as MasterClass implement DRM to make sure only enrolled students can engage with content.
- Gaming companies such as Nintendo use DRM to bind software access to license keys, which means only legitimate users can play.
How DRM video protections works
Securing content published online is no easy feat, and the only reason DRM video protection works is by combining two sophisticated technologies: advanced data encryption and access control.
The technology behind DRM
As the first step in DRM, encryption is the process of encoding video data into a format that can only be deciphered and viewed with a correlating decryption key. This process is essential as it means that even if content falls into unauthorized hands, it’s inaccessible without the key.
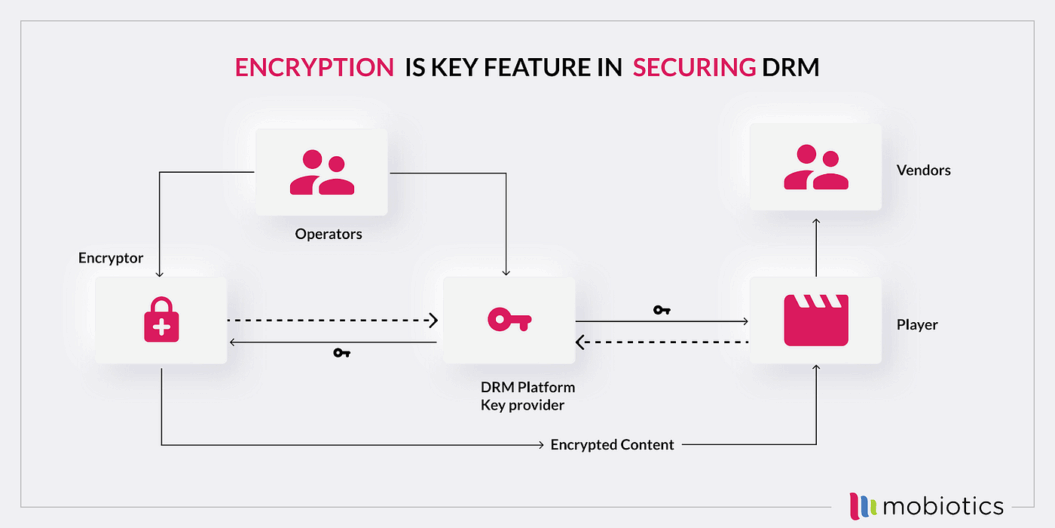
For instance, DRM platforms use Transport Layer Security (TLS) to encrypt data as it travels between servers and viewers to maintain security throughout the delivery process.
Next, access control systems, such as license keys or authentication tokens, verify user authenticity, and only then grant decryption keys, making the content viewable.
These steps ensure that only users with valid authorization, such as an active subscription, are able to access the content.
The DRM workflow
DRM providers follow a structured workflow to ensure they protect creators’ content.
First, when a user requests access to content, their device sends a message to a DRM license server, which contains authentication details (user ID or token).

The server then evaluates these credentials, and verifies if the user is active, subscribed, and has permissions to view the content. If true, the server then provides the decryption key, initiating video playback.
DRM doesn’t stop here, though. During playback, top DRM platforms implement restrictions such as prohibiting screen recording or downloading the content. They can also monitor for account sharing, which can stop viewing rights.
This process protects the creator’s intellectual property while offering a desirable viewing experience.
Why do video creators and businesses need DRM?
DRM isn’t just about stopping piracy – it’s about protecting your business. It keeps your videos from being stolen or shared without permission, helps you stay compliant with copyright laws, and makes sure only paying users get access.
Whether you’re selling courses, running a membership site, or hosting gated webinars, DRM helps you keep control, earn revenue, and stay protected.
First, DRM prevents unauthorized access, piracy, and content accessibility on the dark web. Take, for example, a yoga coach’s premium video series, which, if pirated and distributed without DRM, would undermine that creator’s business.
For B2B SaaS businesses offering gated video demos or webinars as part of their lead generation funnel, DRM helps protect proprietary content while also ensuring quality control.
DRM also helps enforce your monetization model – whether that’s subscriptions, pay-per-view, or limited-time rentals. Let’s say someone cancels their membership – DRM can automatically cut off their access. Or if you’re offering a 72-hour rental, it makes sure the video disappears right on time. That way, you’re in full control of how your content is consumed.
It also helps you stay compliant with copyright laws like the DMCA, reducing the risk of takedowns or legal headaches.
The key takeaway? DRM is a foundational requirement for any business that’s serious about video. It protects your content, supports your revenue model, and gives you peace of mind as you grow.
4 types of DRM video protection
As we’ve mentioned, there are two key technological components of DRM – encryption and access controls.
However, different businesses have different content protection requirements. To meet these needs, DRM platforms offer 4 different approaches to securing video content:
Encryption-based DRM
This is the foundation of DRM: scrambling videos with encryption so they can only be viewed by authorized users. Large streaming platforms like Netflix, Disney+ and Amazon Prime Video, all leverage this technology to protect their video libraries.
If your company uses unified communication services to train staff or engage clients via video, securing those streams with DRM ensures they don’t get leaked or misused.
Token-based DRM authentication
Token-based DRM builds on encryption-based DRM, by issuing time-sensitive keys that are tethered to a user’s account or device. The main benefit of token-based DRM is to prevent password sharing.
Digital watermarking
Digital watermarking is a way for creators to trace any leak back to the source. By embedding invisible markers into videos, the watermark reveals which account leaked the content, acting as a deterrent for pirating activity and also restricting users with a history of illegal behavior.
Geo-restrictions and IP blocking
Compliance with regional licensing is of great importance to creators. Thus, geo-restrictions and IP blocking allow creators to limit content access depending on physical location. An example of this would be a creator restricting a live-streamed event to viewers in the US to comply with distribution rights, with DRM geo-restrictions enforcing these boundaries.
Combined, these 4 types of DRM video protection allow creators to customize their strategy based on their business location, audience, and legal responsibilities.
How to implement DRM for your video content
While clearly essential to any modern video creator or anyone working on an inbound marketing strategy, implementing DRM can run the risk of compromising user experience. Follow these 6 steps to ensure you find the right balance:
1. Choose the right DRM provider
The first step is to select a DRM provider that matches your technical and operational needs.
Ideally, look for one compatible with major platforms (iOS, Android, smart TVs) and standards like Widevine or FairPlay. This will make integration with other programs far easier.
Next, prioritize providers with advanced security features, particularly watermarking and anti-screen-recording capabilities. These are essential to address piracy risks.
Finally, if you plan on having thousands of viewers, confirm the provider’s ability to scale and maintain performance under system strain.
2. Integrate DRM with your video platform
Once you’ve got the right provider, you must integrate DRM with your video platform using APIs or software development kits (SDKs) to embed encryption and access controls into your content library.
3. Set up access control rules
Next, configure access control rules to align with your monetization strategy.
For subscription platforms, grant access exclusively to active members, revoking keys upon cancellation. Rental models can restrict viewing to a specific timeframe, such as 72 hours, while one-time purchases may permit indefinite access limited to designated devices.
Additional controls, such as restricting simultaneous streams or blocking VPN connections, enhance security.
4. Test and monitor DRM performance
Once your DRM process is running, testing and monitoring its performance is essential to ensure a consistent viewer experience.
You should conduct playback tests across devices to verify content streams properly, and always use analytics to monitor playback errors or unauthorized access attempts.
5. Regularly update DRM settings
With pirating techniques constantly developing, you must also frequently and consistently update DRM settings to protect your content.
Advances in screen-recording tools or hacking methods may exploit outdated protections, necessitating stronger encryption or watermarking. Collaborate with your provider to adopt current standards and review access rules every few months to address any vulnerabilities.
6. Combine DRM with other security measures
Finally, supplement DRM to achieve comprehensive protection.
Basics like strong password requirements (a combination of upper case, lower case, numbers and symbols) prevent unauthorized logins, while other features such as VPN detection help enforce geo-restrictions – as using a VPN often circumnavigates rudimentary location detection systems.
Also, server-side protections, such as domain-locking, can block unauthorized embeds. These combined measures ensure digital support for viewers and establish solid content security.
DRM challenges and how to overcome them
While DRM remains essential, there are several common challenges creators face when trying to protect their video content.
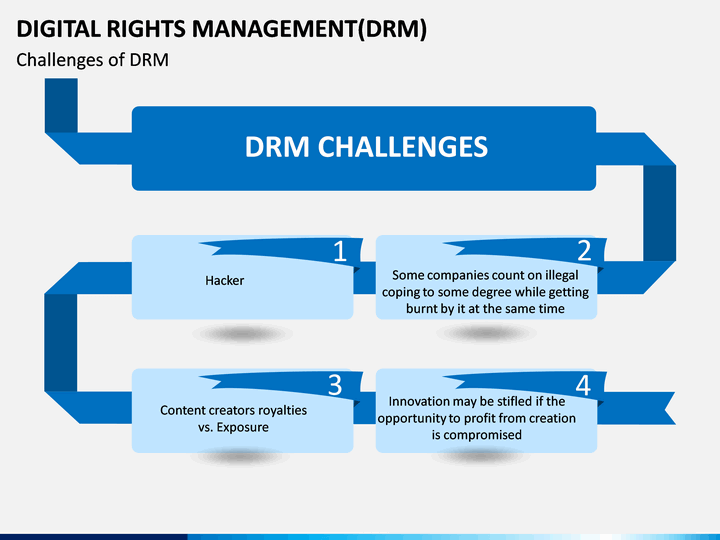
Cybersecurity threats – These can completely undermine any DRM strategy. Malware, data breaches or stolen credentials can lead to identity theft and even expose a creator’s entire library. To prevent this creators should look for DRM platforms that employ two-factor authentication (2FA), multi-factor authentication (MFA) and intrusion detection systems.
Device compatibility – This is another significant obstacle, which generally comes down to the DRM provider. Look for a platform that prioritizes support across all devices for a consistent, high-quality viewing experience.
Cost – DRM platforms can seem pricey at first, but that’s because they’re doing a lot behind the scenes: encrypting content, managing access, blocking piracy, and helping you stay compliant with legal requirements. When you think about the revenue you’re protecting (and the potential losses from leaks or unauthorized sharing), it’s a smart investment.
One way to keep costs manageable is by choosing an all-in-one video platform with built-in DRM tools. That way, you avoid the extra spend and complexity of stitching together multiple third-party solutions.
Protect your video content with DRM
Digital Rights Management is a critical tool for video creators and businesses seeking to secure their content and revenue.
Through encryption, access controls, watermarking and geo-restrictions, DRM prevents unauthorized access and ensures compliance with copyright regulations while preventing content creators revenue streams.
By adopting DRM, creators can confidently focus on their creative personal branding, producing high-quality content, assured that their digital assets are protected and their business is positioned for sustained success.
For details on Uscreen’s content protection strategies, please see our Content Protection and Digital Rights Management page.






